It’s always better to Read The Fine Manual (or run perl afterglow.pl -h for the more updated helpfile)…though it’s not really that well documented 😛 Afterglow allows for two column inputs, rather than us having to do weird tricks to make them 3-column.
(Note to self: get the raw data with fields in the order that you want where possible/faster, rather than pumping it through sed. Makes for good practice though.)
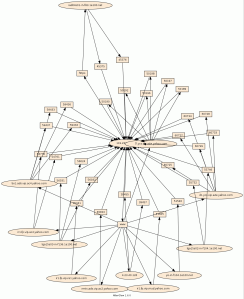
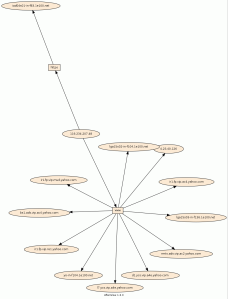
Using the csv file containing userids (visualized in yellow) and IPs (visualized in green) over the past few months from Splunk, here’re the results of some of the experiments.
Oh, for the Windows users, you can use type instead of cat 😉
First test using GraphViz’s neato to layout:
perl afterglow.pl -b 1 -i <infile> -c color.properties -t | neato -Tgif -o output.gif

Second test using fdp:
perl afterglow.pl -b 1 -i <infile> -c color.properties -t | fdp -Tgif -o output.gif

Third test using sfdp:
No command here, you should have noticed the pattern from the first two…

Last test using twopi:
According to the GraphViz site, twopi’s more suited for visualizing stuff like telecommunications flows.