[17 Feb edit: updated the information and added in the link to the spreadsheet]
One of my weird(er) interests is to collect spam samples, not all spam though, the specific ones that were sent from friends’ email accounts. I’ve even asked for people to send me samples of such spam to me back in 2011 (the call for samples still stands though. More spam! More spam!).
What these spammers do with compromised email accounts is to send out spam using their email identities, in the hopes that someone would click through, and you know the rest. What’s not very effective of such spam campaigns though, is that these spam would only contain a single URL in the body with no subject line at all. Good for circumventing spam filters, not so good for getting even the careless to click through. Lucky for us.
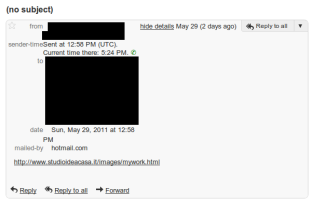
While the volume of such spam mails have been coming in at a trickle’s pace, they have always been coming in all these years. The situation changed all of a sudden since yesterday:
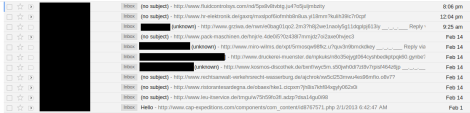
While there have been Yahoo! Webmail XSS vulnerabilities publicly known, and even sold in underground markets granting illegal access to Yahoo! Webmail accounts, this is still weird: Why would these accounts be used to send so much spam all of a sudden? Did somebody accidentally dispatch a massive spam job through all the Yahoo accounts they had control over?
(If you have a Yahoo! Webmail account, it is highly recommended that you change your password (to a good one), and make sure that no one else has any way of regaining access to your webmail identity.)
After some digging around, the trail (all the redirected requests triggered AV alerts) becomes pretty obvious. Looks like someone got greedy (or careless) here, because all the trails end at the same point…
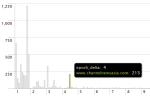
Here’re some of the findings in spreadsheet form (last update 17 Feb 2013). The links sent in the spam emails are all for .de (German) websites, which in turn redirect to what appears to be a site for work-from-home schemes.

 Note: Although this was created some time back (sorry for sharing this so late), there’re improvements to be made still. Discussions are always welcomed.
Note: Although this was created some time back (sorry for sharing this so late), there’re improvements to be made still. Discussions are always welcomed.